From eScan Wiki
| Revision as of 00:18, 12 August 2014 Webmktg (Talk | contribs) (→Viewing Quarantined Objects Report) ← Previous diff |
Current revision Webmktg (Talk | contribs) (→<b>Configuring the settings</b>) |
||
| Line 14: | Line 14: | ||
| - | The Protection module provides real-time protection to your system against all kinds of viruses and malwares. By default, eScan’s real-time monitor feature monitors and detects your system for any viruses. If any viruses are detected, eScan provides automatic virus pop-up alerts. Whenever eScan finds any infected file, it first tries to disinfected the file, and incase if it finds difficult to disinfect, it quarantines the file to take an action later. It helps you set an action for monitor to take in case of any virus detection. | + | The Protection module provides real-time protection to your system against all kinds of virus and malwares [[including Windows-based malwares, which could easily spread through external devices, such as USB storage device, CD-DVD ROM, Pen drive, or downloads.]] By default, eScan’s real-time monitor feature, monitors and detects your system for any virus. [[eScan provides an automatic virus pop-up alert in case any virus is detected. The first action taken by eScan will be to disinfect the infected file, and in case if it fails to disinfect, it quarantines the file to take an action later. It also helps you to pre-define an action in case of any virus detection.]] |
| - | It monitors and helps you scan mails, archived files, scan packed files, and scan excluded directories, files, and specific file types. | + | It monitors and helps you to scan, mails, archived files, scan packed files, and scan excluded directories, files, and specific file types. |
| - | The viruses log gets created in a table format and a detailed graphical representation of the number of files infected, quarantined, deleted, disinfected, and clean files are displayed. | + | The virus log is created in a table format and a detailed graphical representation of the number of files infected, quarantined, deleted, disinfected, and clean files are displayed. |
| - | You can modify the default settings as per your requirement. | + | [[You can modify the default settings as per your requirement.]] |
| - | + | [[The Protection module is divided in to two sections — Configuration and Reports]] | |
| - | The Protection module is divided in two sections — Configuration and Reports | + | |
| ==<b>Configuration</b>== | ==<b>Configuration</b>== | ||
| - | This section provides you information on protection status and type of action taken on the infected object. You can also configure eScan protection settings. | + | [[This section provides the details on protection status and the type of action taken on the infected object. You can also configure eScan protection settings.]]<ul> |
| - | <ul> | + | <li>Protection Status: [[It displays the status of eScan protection, whether it is in started or stopped mode]].</li> |
| - | <li>Protection Status: It displays the status of eScan protection, whether it is in started or stopped mode.</li> | + | <li>Action: [[It displays the type of action eScan protection has taken on the infected object.]]</li> |
| - | <li>Action: It displays the type of action eScan protection has taken on the infected object.</li> | + | <li>Start/stop: [[Click this button to start/stop the eScan protection.]]</li> |
| - | <li>Start/stop: Click this button to start/stop the eScan protection.</li> | + | <li>Settings: [[Click this button to configure protection status, scan, and log settings.]] |
| - | <li>Settings: Click this button to configure protection status, scan, and log settings.</li> | + | </li> |
| - | </ul> | + | </ul><b>Note:</b> [[A normal user doesn't have the privilege to access the Start/Stop and the Settings feature. In order to access them the user has to login as an administrator. Refer the note under the Logging On section to login as an administrator.]] |
| - | + | ||
| - | <b>Note:</b> A normal user doesn’t have the privilege to access the Start/stop and the Settings feature. In order to access them the user has to login as an administrator. Refer the note under the Logging On section to login as an administrator. | + | |
| ==<b>Reports</b>== | ==<b>Reports</b>== | ||
| - | This section provides you information on the total file scanned, dangerous object found, and last scanned file. You can view statistics report of the files, list of quarantined objects, and files report. | + | [[This section provides you information on the total file scanned, dangerous object found, and last scanned file. You can view statistics report of the files, list of quarantined objects, and files report.]]<ul> |
| - | <ul> | + | <li>Total file scanned: [[It displays the total number of files scanned by eScan protection.]]</li> |
| - | <li>Total file scanned: It displays the total number of files scanned by eScan protection.</li> | + | <li>Dangerous object found: [[It displays the total number of infected objects detected by eScan protection.]]</li> |
| - | <li>Dangerous object found: It displays the total number of infected objects detected by eScan protection.</li> | + | <li>Last scanned file: [[It displays the path of the last scanned file.]]</li> |
| - | <li>Last scanned file: It displays the path of the last scanned file.</li> | + | <li>View statistics: [[Click this button to view the virus file report in the form of a 3D pie chart.]]</li> |
| - | <li>View statistics: Click this button to view the virus file report in the form of a 3-D pie chart.</li> | + | <li>View quarantined objects: [[Click this button to view the list of quarantined objects with path and total number of quarantined objects.]]</li> |
| - | <li>View quarantined objects: Click this button to view the list of quarantined objects with path and total number of quarantined objects.</li> | + | <li>View report: [[Click this button to view the log of the activities performed.]]</li> |
| - | <li>View report: Click this button to view the log of the activities performed.</li> | + | |
| </ul> | </ul> | ||
| - | You can do the following activities: | + | [[You can do the following activities]]: |
| <ul> | <ul> | ||
| - | <li>Starting and Stopping eScan real-time protection</li> | + | <li>[[Start and Stop eScan real-time protection]]</li> |
| - | <li>Configuring the settings</li> | + | <li>[[Configure the settings]]</li> |
| - | <li>Viewing Statistics</li> | + | <li>[[View Statistics]]</li> |
| - | <li>Viewing Quarantined Objects</li> | + | <li>[[View Quarantined Objects]]</li> |
| - | <li>Viewing Report</li> | + | <li>[[View Reports]]</li> |
| </ul> | </ul> | ||
| Line 61: | Line 57: | ||
| | | ||
| - | ==<b>Starting and Stopping eScan Monitor</b>== | + | ==<b>Starting and Stopping eScan [[real-time protection]]</b>== |
| - | By default, eScan real-time monitoring starts after you add a license key. This feature is available only to an administrator. The <b>eScan Anti-Virus</b> | + | By default, eScan real-time [[protection starts after the installation]]. The <b>eScan Anti-Virus</b> |
| - | [[Image:eScan for Mac - Monitor status icon green.jpg]] | + | [[Image:eScan for Mac - Monitor status icon green.jpg]] icon gets mounted on the toolbar when you install eScan for Mac on your system. By default, monitor is in <b>Start</b> mode. |
| - | icon gets mounted on the toolbar when you install eScan for Mac on your system. By default, monitor is in <b>Start</b> mode. | + | |
| You can start and stop eScan monitor in the following ways: | You can start and stop eScan monitor in the following ways: | ||
| Line 103: | Line 98: | ||
| - | {| id="table1" style="border-collapse: collapse; border-color: #000000; padding: 1px" width="110%" border="1" cellspacing="1" | + | {| id="table1" style="border-collapse: collapse; border-color: #000000; padding: 1px" width="100%" border="1" cellspacing="1" |
| |- bgcolor="#ffffff" valign="center" | |- bgcolor="#ffffff" valign="center" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="30%" height="25" bgcolor="#D0E7F6" align="left" | | | style="border-style: solid; border:"1"; border-width: 1px" width="30%" height="25" bgcolor="#D0E7F6" align="left" | | ||
| Line 110: | Line 105: | ||
| <font face="Arial">'''Description'''</font> | <font face="Arial">'''Description'''</font> | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "3" align="left" | <font face="Arial">'''Scan Settings'''</font> | + | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "2" align="left" | <font face="Arial">'''Scan Settings'''</font> |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial">'''Action in case of virus detection'''</font> | + | | style="border-style: solid; border:"1"; border-width: 1px" width="270" align="left" valign=top | <font face="Arial">'''Action in case of virus detection'''</font> |
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |It indicates a type of action which you want eScan real-time protection to take, in case of virus detection. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="280" align="left" valign="center" |It indicates a type of action which you want eScan real-time protection to take, in case of virus detection. |
| By default, Disinfect (if not possible, quarantine file) option is selected. Following are the types of actions: | By default, Disinfect (if not possible, quarantine file) option is selected. Following are the types of actions: | ||
| Line 127: | Line 122: | ||
| :• <b>Quarantine:</b> It directly quarantines the infected object. Select an appropriate option from the box. | :• <b>Quarantine:</b> It directly quarantines the infected object. Select an appropriate option from the box. | ||
| - | . | ||
| - | |||
| - | Select an appropriate option from the box. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Mails'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Mails'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |It indicates the mail files. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |It indicates the mail files. |
| By default, it is selected. Select this check box if you want eScan real-time protection to scan mails. | By default, it is selected. Select this check box if you want eScan real-time protection to scan mails. | ||
| - | |||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Archives'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Archives'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | It indicates the archived files, such as zip, rar, and so on. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" | It indicates the archived files, such as zip, rar, and so on. |
| Select this check box if you want eScan real-time protection to scan archived files. | Select this check box if you want eScan real-time protection to scan archived files. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Packed'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Packed'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |It indicates the compressed executable. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |It indicates the compressed executable. |
| By default, it is selected. Select this check box if you want eScan real-time protection to scan packed files. | By default, it is selected. Select this check box if you want eScan real-time protection to scan packed files. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Exclude directories and files'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Exclude directories and files'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |Select this check box if you want eScan real-time protection to exclude directories and files from scanning. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |Select this check box if you want eScan real-time protection to exclude directories and files from scanning. |
| - | The [[Image:Exclude icon.jpg]] icon is available only when you select <b>Exclude directories and files</b> check box. Click the [[Image:Exclude icon.jpg]] icon and then click the <b>Browse</b> button to select the | + | The [[Image:Exclude icon.jpg]] icon is available only when you select <b>Exclude directories and files</b> check box. Click the [[Image:Exclude icon.jpg]] icon and then click the <b>Browse</b> button to select the directories and files that you want to exclude. |
| - | + | ||
| - | directories and files that you want to exclude. | + | |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Exclude file types'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Exclude file types'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |Select this check box if you want eScan real-time protection to exclude specific files. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |Select this check box if you want eScan real-time protection to exclude specific files. |
| The [[Image:Exclude icon.jpg]] icon is available only when you select <b>Exclude file types</b> check box. Click the [[Image:Exclude icon.jpg]] icon and then click the <b>Browse</b> button to select the directories and files that you want to exclude. | The [[Image:Exclude icon.jpg]] icon is available only when you select <b>Exclude file types</b> check box. Click the [[Image:Exclude icon.jpg]] icon and then click the <b>Browse</b> button to select the directories and files that you want to exclude. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "3" align="left" | <font face="Arial">'''Log Options'''</font> | + | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "2" align="left" | <font face="Arial">'''Log Options'''</font> |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Log level'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Log level'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |It indicates a type of log level which you want eScan real-time protection to display. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |It indicates a type of log level which you want eScan real-time protection to display. |
| By default, Report log option is selected. Following are the type of log level: | By default, Report log option is selected. Following are the type of log level: | ||
| Line 172: | Line 161: | ||
| :• <b>Detail Log:</b> Indicates the log of all the details necessary to diagnose any problem as well as to know the more details of scanned object. | :• <b>Detail Log:</b> Indicates the log of all the details necessary to diagnose any problem as well as to know the more details of scanned object. | ||
| - | |||
| Select an appropriate option from the box. | Select an appropriate option from the box. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Report lifetime days'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Report lifetime days'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |It indicates the number of days up to which you want to save the report. For example, if you type 10 days, then the report is saved only for 10 days, starting from the date when you have modified. By default, 365 days appear. The minimum number limit is 1 and maximum number limit is 365. Type the days or select the specific number of days you want to change. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |It indicates the number of days up to which you want to save the report. For example, if you type 10 days, then the report is saved only for 10 days, starting from the date when you have modified. By default, 365 days appear. The minimum number limit is 1 and maximum number limit is 365. Type the days or select the specific number of days you want to change. |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Display popup alert'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Display popup alert'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |By default, it is selected. Select this check box if you want eScan real-time protection to display virus pop-up alerts | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |By default, it is selected. Select this check box if you want eScan real-time protection to display virus pop-up alerts whenever any viruses are detected, provided monitor is in <b>Turn On</b> mode. |
| - | + | ||
| - | whenever any viruses are detected, provided monitor is in <b>Turn On</b> mode. | + | |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Block USB storage device(s)'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Block USB storage device(s)'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |Select this option to block access to the USB Storage device or CD/DVD-ROM connected to the Mac. This will prevent spreading of any suspicious malware that generally spreads from one machine to other through USB storage devices, hence reducing the threat of infection from secondary storage devices like USB Drives and CD/DVD-ROMs on your machine. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |Select this option to block access to the USB Storage device or CD/DVD-ROM connected to the Mac. This will prevent spreading of any suspicious malware that generally spreads from one machine to other through USB storage devices, hence reducing the threat of infection from secondary storage devices like USB Drives and CD/DVD-ROMs on your machine. |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Set to default'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Set to default'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |Click this link to set the default settings. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="330" align="left" valign="center" |Click this link to set the default settings. |
| |} | |} | ||
| Line 225: | Line 211: | ||
| [[Image:Viewing Quarantined Objects.jpg|center]] | [[Image:Viewing Quarantined Objects.jpg|center]] | ||
| | | ||
| - | |||
| - | ==Viewing Report== | ||
| - | |||
| - | eScan protection creates a log of the activities performed. It displays the name of the file infected, date on which file got infected, name of the virus found, and the status of the virus. It displays the log based on the number of days you have set in Report lifetime days field, under Log Options section. | ||
| - | :• View the details as required. | ||
Current revision
eScan Anti-Virus Security for Mac Version 5.x Online Help
Contents |
Protection
The Protection module provides real-time protection to your system against all kinds of virus and malwares including Windows-based malwares, which could easily spread through external devices, such as USB storage device, CD-DVD ROM, Pen drive, or downloads. By default, eScan’s real-time monitor feature, monitors and detects your system for any virus. [[eScan provides an automatic virus pop-up alert in case any virus is detected. The first action taken by eScan will be to disinfect the infected file, and in case if it fails to disinfect, it quarantines the file to take an action later. It also helps you to pre-define an action in case of any virus detection.]]
It monitors and helps you to scan, mails, archived files, scan packed files, and scan excluded directories, files, and specific file types.
The virus log is created in a table format and a detailed graphical representation of the number of files infected, quarantined, deleted, disinfected, and clean files are displayed.
You can modify the default settings as per your requirement. The Protection module is divided in to two sections — Configuration and Reports
Configuration
This section provides the details on protection status and the type of action taken on the infected object. You can also configure eScan protection settings.- Protection Status: It displays the status of eScan protection, whether it is in started or stopped mode.
- Action: It displays the type of action eScan protection has taken on the infected object.
- Start/stop: Click this button to start/stop the eScan protection.
- Settings: Click this button to configure protection status, scan, and log settings.
Reports
This section provides you information on the total file scanned, dangerous object found, and last scanned file. You can view statistics report of the files, list of quarantined objects, and files report.- Total file scanned: It displays the total number of files scanned by eScan protection.
- Dangerous object found: It displays the total number of infected objects detected by eScan protection.
- Last scanned file: It displays the path of the last scanned file.
- View statistics: Click this button to view the virus file report in the form of a 3D pie chart.
- View quarantined objects: Click this button to view the list of quarantined objects with path and total number of quarantined objects.
- View report: Click this button to view the log of the activities performed.
You can do the following activities:
- Start and Stop eScan real-time protection
- Configure the settings
- View Statistics
- View Quarantined Objects
- View Reports
Starting and Stopping eScan real-time protection
By default, eScan real-time protection starts after the installation. The eScan Anti-Virus
![]() icon gets mounted on the toolbar when you install eScan for Mac on your system. By default, monitor is in Start mode.
icon gets mounted on the toolbar when you install eScan for Mac on your system. By default, monitor is in Start mode.
You can start and stop eScan monitor in the following ways:
- On the eScan for Mac window, under Configuration section, click the Stop button to stop eScan real time protection.
When you click Stop button, the Protection status changes from Started (in green colour) to Stopped (in red colour) and the eScan Anti-Virus
 icon in green changes to eScan Anti-Virus
icon in green changes to eScan Anti-Virus  icon in red.
icon in red. - On the eScan for Mac window, under Configuration section, click the Start button to start eScan real time protection.
When you click Start button, the Protection status changes from Stopped (in red colour) to Started (in green colour) and the eScan Anti-Virus
 icon in red changes to eScan Anti-Virus
icon in red changes to eScan Anti-Virus  icon in green.
icon in green. - On upper-right corner of the window, click eScan real time protection is ON
 icon, and then click Disable eScan Protection option to stop eScan protection.
On upper-right corner of the window, click eScan real time protection is OFF
icon, and then click Disable eScan Protection option to stop eScan protection.
On upper-right corner of the window, click eScan real time protection is OFF  icon, and then click Enable eScan Protection option to start eScan protection.
icon, and then click Enable eScan Protection option to start eScan protection.
OR
Configuring the settings
Real-time Protection enables you to configure the settings as per your requirement. eScan’s real-time protection scans and monitors your system for any viruses. In case of virus detection, eScan takes an immediate action and displays the virus pop-up alerts.
You can scan mails, archives, and packed files, and also you can exclude specific directories, files, and file types.
During scanning, eScan creates a log of all the activities performed. There are different types of log level that gets created, and you can select the type of log you want to view.
To configure the settings
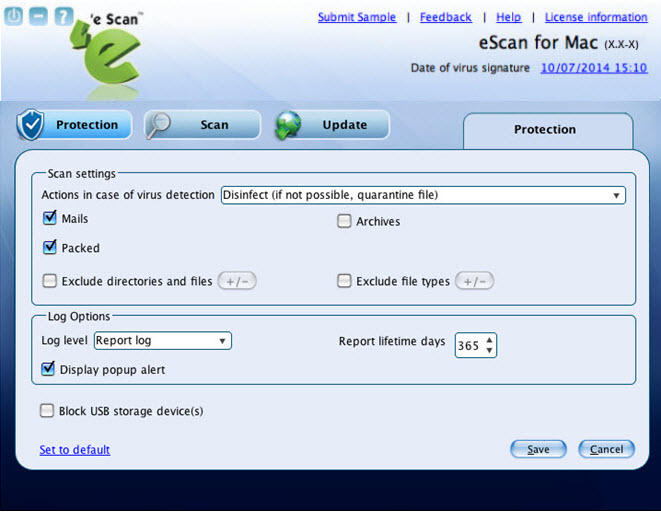
On the eScan for Mac window, under Configuration section, click the Settings button. The Protection tab appears
- On the eScan for Mac window, under Configuration section, click the Settings button. The Protection tab appears
- On the Protection tab, specify the following field details.
- Click the Save button.
The settings get saved.
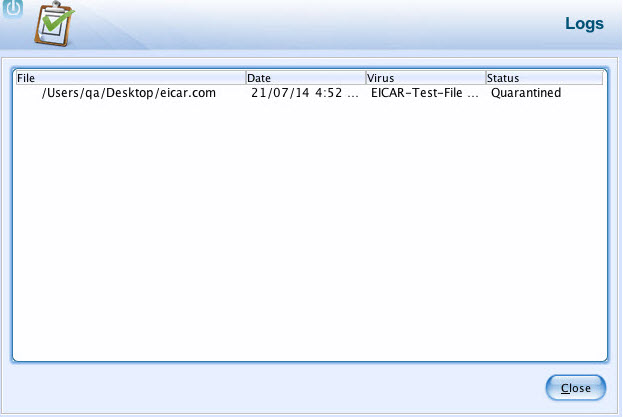
Viewing Log
eScan protection module creates a log of the activities performed. It displays the name of the file infected, date on which file got infected, name of the virus found, and the status of the virus.
- View the details as required
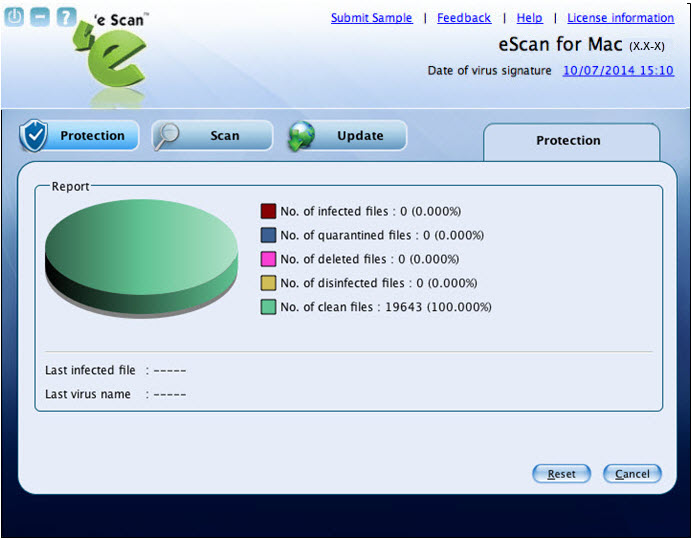
Viewing Statistics
eScan protection module creates a virus file report in the form of a 3-D pie chart, in which each legend represents a specific colour for a specific type of a virus file. Each legend provides you the details of the number of infected, quarantined, deleted, disinfected, and clean files, and also name of the last infected file, and last virus name. When the eScan protection status is in stop mode, the 3-D pie chart is displayed in gray colour and when eScan protection status is in start mode, the 3-D pie chart is displayed in green colour for clean files and other colours are displayed based on the colour assigned to the type of file.
- • View the details as required.
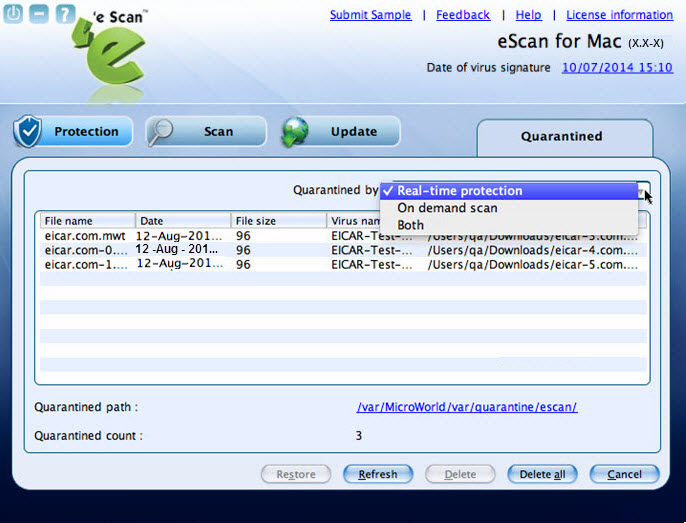
Viewing Quarantined Objects Report
eScan protection module creates a log report of the quarantined objects. The infected objects are quarantined during scanning based on the option you have selected under Scan settings section. You can view the file(s) quarantined by, Real-time protection, On demand Scan or Both options under the Quarantined by drop-down field. You can view and delete a specific file or delete all infected files by clicking Delete all button. You can also restore the deleted files, if needed. It displays the list of infected files that have been quarantined with file name, date, file size, and virus name. It also displays the path where quarantined files are saved with number of quarantined files.