From eScan Wiki
| Revision as of 01:57, 13 August 2014 Webmktg (Talk | contribs) (→<b> Scan </b>) ← Previous diff |
Current revision Webmktg (Talk | contribs) (→<b> Scan </b>) |
||
| Line 5: | Line 5: | ||
| __TOC__ | __TOC__ | ||
| + | |||
| + | <h2 id="mp-tfp-h2" style="margin:0; background:#95C33D; font-size:120%; font-weight:bold; border:10 solid #afa3bf; text-align:left; color:#000; padding:0.2em 0.4em">eScan Anti-Virus Security for Mac Version 5.x Online Help</h2> | ||
| == <b> Scan </b>== | == <b> Scan </b>== | ||
| - | The Scan module helps you to perform on-demand scanning on the selected files/directories, home directories, and my computer. Apart from system scanning, you can scan all the connected USB’s and CD-ROM | + | The Scan module helps you to perform on-demand scanning on the selected files/directories, home directories, and my computer. Apart from system scanning, you can scan all the connected USB devices and CD-ROM devices, through auto and manual scan feature. You can pre-define actions to be taken in case of virus detection and the logs are maintained for all the actions taken. |
| - | + | ||
| - | devices, through auto and manual scan feature. You have various options to set for eScan to take action when any viruses are detected. The logs of scanning can be located at a specific location with a level of log | + | |
| - | + | ||
| - | you want to view. You can quarantine the suspected or infected files, and also perform real-time monitoring on files and reports. | + | |
| - | + | ||
| Click this module, to access the scan screen. On the screen, you can configure the following settings: | Click this module, to access the scan screen. On the screen, you can configure the following settings: | ||
| Line 23: | Line 20: | ||
| ::<li><h5><b>Scan My Computer:</b></h5> Click this link, if you want to scan the entire system.</li> | ::<li><h5><b>Scan My Computer:</b></h5> Click this link, if you want to scan the entire system.</li> | ||
| - | ::<li><h5><b>Scan home directories:</b></h5> Click this link, if you want to scan all files and folders of home directories of the logged in user.</li> | + | ::<li><h5><b>Scan home directories:</b></h5> Click this link, if you want to scan all files and folders of home directories of the logged in user.</li> |
| ::<li><h5><b>Custom Scan:</b></h5> Click this link, if you want to scan specific files/ directories.</li> | ::<li><h5><b>Custom Scan:</b></h5> Click this link, if you want to scan specific files/ directories.</li> | ||
| - | ::<li><h5><b>Scan USB devices:</b></h5> Click this link, if you want to scan any specific USB storage devices like Pen drive, CD-ROM device, and so on. Automatic scanning of the USB storage devices, as and | + | ::<li><h5><b>Scan USB devices:</b></h5> Click this link, if you want to scan any specific USB storage devices like Pen drive, CD-ROM device, and so on. Automatic scanning of the USB storage devices, as and when it is connected and mounted, is always active by default.</li> |
| - | + | ||
| - | when it is connected and mounted, is always active by default.</li> | + | |
| *<h3><b>Additional Options:</b></h3> | *<h3><b>Additional Options:</b></h3> | ||
| Line 51: | Line 46: | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial">'''Action in case of virus detection'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial">'''Action in case of virus detection'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |It indicates a type of action which you want eScan real-time scanner to take, in case of virus detection. | + | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" |''It indicates a type of action to be taken in case of virus detection.''By default, Disinfect (if not possible, quarantine file) option is selected. Following are the types of actions: |
| - | By default, Disinfect (if not possible, quarantine file) option is selected. Following are the types of actions: | + | |
| - | :• <b>Log Only:</b> It indicates or alerts the user about the infection detected. . | + | :• <b>Log Only:</b> It indicates [[or alerts]] the user about the infection detected. |
| :• <b>Disinfect (if not possible, log):</b> It tries to disinfect and if disinfection is not possible it logs the information of only the infected object. | :• <b>Disinfect (if not possible, log):</b> It tries to disinfect and if disinfection is not possible it logs the information of only the infected object. | ||
| Line 76: | Line 70: | ||
| Select an appropriate option from the box. | Select an appropriate option from the box. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "3" align="left" | <font face="Arial">'''Scan Settings'''</font> | + | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "2" align="left" | <font face="Arial">'''Scan Settings'''</font> |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| Line 89: | Line 83: | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Heuristic'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Heuristic'''</font> | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | | ||
| - | Select this check box if you want eScan real-time protection to exclude directories and files from scanning. | + | ''Select this check box if you want eScan real-time protection to exclude directories and files from scanning. |
| - | Click the icon and then click the Browse button to select the directories and files that you want to exclude. | + | Click the [[Image:Exclude icon.jpg]] icon and then click the Browse button to select the directories and files that you want to exclude.'' |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Cross file system'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Cross file system'''</font> | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | | ||
| - | Select this check box if you want eScan real-time protection to exclude specific files. | + | ''Select this check box if you want eScan real-time protection to exclude specific files. |
| - | Click the icon and then click the Browse button to select the directories and files that you want to exclude. | + | Click the [[Image:Exclude icon.jpg]] icon and then click the Browse button to select the directories and files that you want to exclude.'' |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Archives'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Archives'''</font> | ||
| Line 106: | Line 100: | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Follow symbolic links'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Follow symbolic links'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | It indicates the symbolic links that allows you to access one file from another through links. This option specifies | + | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | It indicates the symbolic links that allows you to access one file from another through links. This option specifies the on-demand scanner whether to resolve the symbolic link before actually scanning the object or to skip any such links. |
| - | + | ||
| - | the on-demand scanner whether to resolve the symbolic link before actually scanning the object or to skip any such links. | + | |
| Select this check box if you want to follow symbolic links. | Select this check box if you want to follow symbolic links. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "3" align="left" | <font face="Arial">'''Log Settings'''</font> | + | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "2" align="left" | <font face="Arial">'''Log Settings'''</font> |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Log location'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Log location'''</font> | ||
| Line 119: | Line 111: | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Log level'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Log level'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | It indicates a type of log level which you want eScan real-time protection to display. Following are the type of log | + | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | It indicates a type of log level that you want eScan real-time protection to display. Following are the type of log level: |
| - | + | ||
| - | level: | + | |
| By default, infected is selected. | By default, infected is selected. | ||
| Line 128: | Line 118: | ||
| :• <b>Infected:</b> This option will specify only details of the infected objects in the eScan log. | :• <b>Infected:</b> This option will specify only details of the infected objects in the eScan log. | ||
| - | :• <b>Minimum:</b> This option will specify only a minimum detail of the objects scanned in the eScan log. | + | :•<b>Minimum:</b> This option will specify only a minimum detail of the objects scanned in the eScan log. |
| Click an appropriate option. | Click an appropriate option. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "3" align="left" | <font face="Arial">'''Exclude Options'''</font> | + | | style="border-style: solid; border:"1"; border-width: 1px" width="300" colspan = "2" align="left" | <font face="Arial">'''Exclude Options'''</font> |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Files and directories'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Files and directories'''</font> | ||
| - | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | Click the [[Image:Exclude icon.jpg]] icon and then click the <b>Browse</b> button to select the files and directories | + | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | Click the [[Image:Exclude icon.jpg]] icon and then click the <b>Browse</b> button to select the files and directories that you want to exclude from real-time scanning. |
| - | + | ||
| - | that you want to exclude from real-time scanning. | + | |
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''File types'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''File types'''</font> | ||
| Line 150: | Line 138: | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Restore global settings'''</font> | | style="border-style: solid; border:"1"; border-width: 1px" width="300" align="left" valign=top | <font face="Arial"> '''Restore global settings'''</font> | ||
| | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | | | style="border-style: solid; border:"1"; border-width: 1px" width="336" align="left" valign="center" | | ||
| - | It indicates the settings of an administrator. It is available only for normal user. | + | It indicates the settings of an administrator. It is available only for a normal user. |
| - | + | ||
| Click this link, if you want to restore global settings. | Click this link, if you want to restore global settings. | ||
| |- bgcolor="#ffffff" | |- bgcolor="#ffffff" | ||
| Line 166: | Line 153: | ||
| - | ::<li><h5><b>Scheduler:</b></h5></li> | + | ::<li><h5><b>[[Scheduler]]:</b></h5></li> |
| - | :The scheduler module helps you to perform scanning on local hard disk drives and selected directories and files on a schedule month, date, hour, minute, and day. Under <b>Options</b> window, you have various | + | :The scheduler module helps you to perform scanning on local hard disk drives and selected directories and files on a scheduled month, date, hour, minute, and day. Under <b>Options</b> window, you have various options to set for eScan to take action when a virus is detected. |
| - | options to set for eScan to take action when any viruses are detected. | + | :This module is available only for an administrator, but a normal user can also access and configure the scheduler settings by logging on as an administrator. It displays the list of scheduled tasks to be executed at a specific time. Click this module, to schedule the tasks for scanning. You can also edit, delete, or purge the scheduled tasks. With <b>Delete</b> button, you can delete any scheduled task, but <b>Purge</b> button is meant only for outdated schedules, wherein if you click <b>Purge</b> button outdated schedules get automatically deleted. |
| - | + | ||
| - | :This module is available only for administrator, but a normal user can also access and configure the scheduler settings by logging on as an administrator. It displays the list of scheduled tasks to be executed at a | + | |
| - | + | ||
| - | specific time. Click this module, to schedule the tasks for scanning. You can also edit, delete, or purge the scheduled tasks. With <b>Delete</b> button, you can delete any scheduled task, but <b>Purge</b> button | + | |
| - | + | ||
| - | is meant only for outdated schedules, wherein if you click <b>Purge</b> button outdated schedules get automatically deleted. | + | |
| | | ||
| Line 182: | Line 163: | ||
| | | ||
| - | :<b>Note:</b> The<b>*Schedule(s) outdated</b> displayed at the lower-left corner of the window indicates the outdated schedules. The schedules, which are run only once, are called outdated schedules. | + | :<b>Note:</b> The<b>*Schedule(s) outdated</b> displayed at the lower-left corner of the window indicates the outdated schedules. The schedules that were run only once, are called outdated schedules. |
| - | + | :When you click <b>Add task</b> button, the following two tabs appear | |
| - | :When you click <b>Add task</b> button, the following two tabs appear: | + | |
| :::::<li><b>Schedule:</b></li> | :::::<li><b>Schedule:</b></li> | ||
| - | :::::It helps you to scan local hard disk/partitions/volumes and selected directories/files. When you select <b>Scan my computer</b> option, eScan scans the entire system. If you want to scan only specific | + | :::::It helps you to scan local hard disk/partitions/volumes and selected directories/files. When you select <b>Scan my computer</b> option, eScan scans the entire system. If you want to scan only specific directories and files, click the <b>Scan following directories and files</b> option, and then click the <b>Browse</b> button to select the directories and files of your choice. |
| - | + | ||
| - | directories and files, click the <b>Scan following directories and files</b> option, and then click the <b>Browse</b> button to select the directories and files of your choice. | + | |
| - | + | ||
| :::::You can schedule the month, date, hour, minute, and day, on which you want to run the task. | :::::You can schedule the month, date, hour, minute, and day, on which you want to run the task. | ||
| Line 211: | Line 188: | ||
| | | ||
| - | [[Image:Scan Scheduler - Options window.jpg|center]] | + | [[Image:MAC Scan Log.jpg|center]] |
| | | ||
Current revision
eScan Anti-Virus Security for Mac Version 5.x Online Help
Contents |
eScan Anti-Virus Security for Mac Version 5.x Online Help
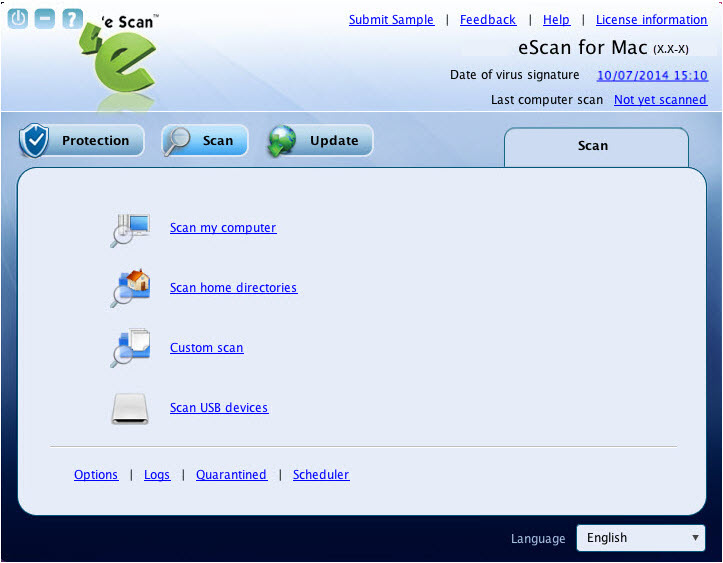
Scan
The Scan module helps you to perform on-demand scanning on the selected files/directories, home directories, and my computer. Apart from system scanning, you can scan all the connected USB devices and CD-ROM devices, through auto and manual scan feature. You can pre-define actions to be taken in case of virus detection and the logs are maintained for all the actions taken. Click this module, to access the scan screen. On the screen, you can configure the following settings:
- [edit]
Scan Options:
- [edit]
Scan My Computer:
Click this link, if you want to scan the entire system. - [edit]
Scan home directories:
Click this link, if you want to scan all files and folders of home directories of the logged in user. - [edit]
Custom Scan:
Click this link, if you want to scan specific files/ directories. - [edit]
Scan USB devices:
Click this link, if you want to scan any specific USB storage devices like Pen drive, CD-ROM device, and so on. Automatic scanning of the USB storage devices, as and when it is connected and mounted, is always active by default.
- [edit]
Additional Options:
- [edit]
Options:
- This option helps you configure scan settings for virus detection.
- On the Options tab, specify the following field details.
- • Log Only: It indicates or alerts the user about the infection detected.
- • Disinfect (if not possible, log): It tries to disinfect and if disinfection is not possible it logs the information of only the infected object.
- • Disinfect (if not possible, delete file): It tries to disinfect and if disinfection is not possible it deletes the infected object.
- • Disinfect (if not possible, quarantine file): It tries to disinfect and if disinfection is not possible it quarantines the infected object.
- • Disinfect (if not possible, rename file): It tries to disinfect and if disinfection is not possible it renames the infected object.
- • Disinfect (if not possible, ask user): It tries to disinfect and if disinfection is not possible it asks user to take an action on the infected object.
- • Delete: It directly deletes the infected object.
- • Quarantine: It directly quarantines the infected object.
- • Rename: It directly renames the infected object.
- • Ask user: It asks user to take an action on the infected object.
- • All: This option will specify a detailed eScan log.
- • Infected: This option will specify only details of the infected objects in the eScan log.
- •Minimum: This option will specify only a minimum detail of the objects scanned in the eScan log.
- Click the Save button.
|
Field |
Description |
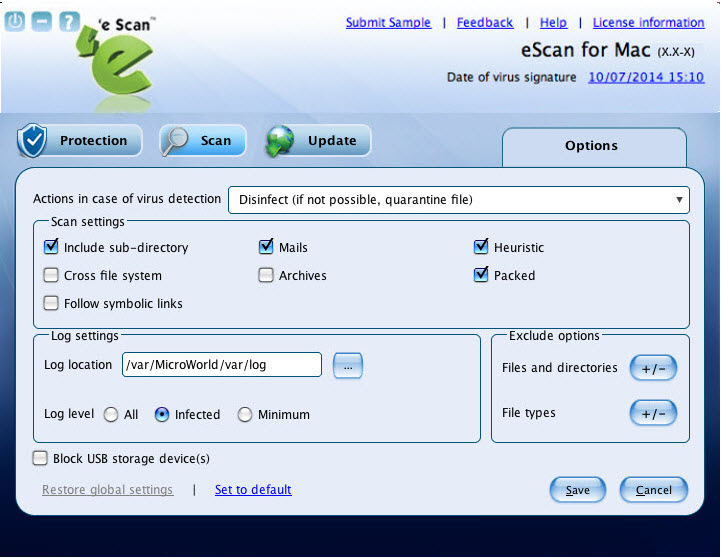
| Action in case of virus detection | It indicates a type of action to be taken in case of virus detection.By default, Disinfect (if not possible, quarantine file) option is selected. Following are the types of actions:
Select an appropriate option from the box. |
| Scan Settings | |
| Include Sub-directory | It indicates the archived files, such as zip, rar, and so on.
Select this check box if you want eScan real-time protection to scan archived files. |
| Mails | It indicates the mail files.
By default, it is selected. Select this check box if you want eScan real-time protection to scan mail files. |
| Heuristic |
Select this check box if you want eScan real-time protection to exclude directories and files from scanning.
Click the |
| Cross file system |
Select this check box if you want eScan real-time protection to exclude specific files.
Click the |
| Archives | It indicates the archived files, such as zip, rar, and so on.
Select this check box if you want eScan real-time protection to scan archived files. |
| Packed | It indicates the compressed executable.
By default, it is selected. Select this check box if you want eScan real-time protection to scan packed files. |
| Follow symbolic links | It indicates the symbolic links that allows you to access one file from another through links. This option specifies the on-demand scanner whether to resolve the symbolic link before actually scanning the object or to skip any such links.
Select this check box if you want to follow symbolic links. |
| Log Settings | |
| Log location | It indicates the location where you want eScan real-time scanner to save the log file.
By default, /var/MicroWorld/var/log location appears. If you want you can change the location.
Click the |
| Log level | It indicates a type of log level that you want eScan real-time protection to display. Following are the type of log level:
By default, infected is selected. Click an appropriate option. |
| Exclude Options | |
| Files and directories | Click the |
| File types |
Click the |
| Block USB storage device(s) |
Select this check box, if you want to block all connected USB’s and CD-ROM storage devices from real-time scanning. |
| Restore global settings |
It indicates the settings of an administrator. It is available only for a normal user. Click this link, if you want to restore global settings. |
| Set to default |
It indicates the default settings set at first time installation. Click this link to set the default settings. |
The settings get saved.
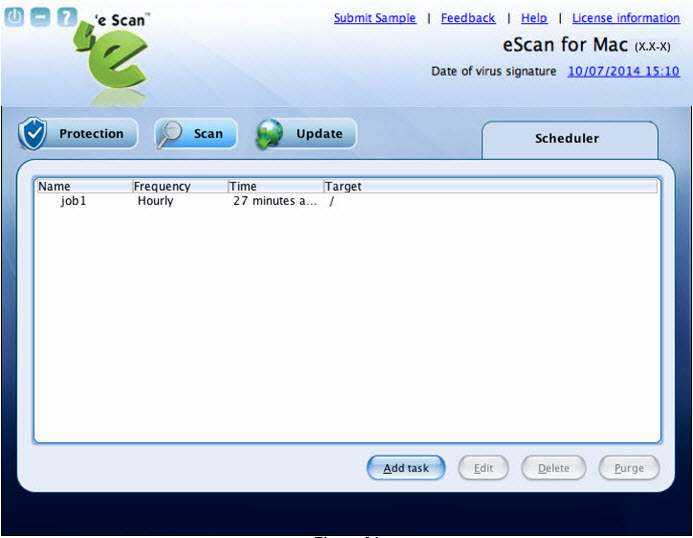
- The scheduler module helps you to perform scanning on local hard disk drives and selected directories and files on a scheduled month, date, hour, minute, and day. Under Options window, you have various options to set for eScan to take action when a virus is detected.
- This module is available only for an administrator, but a normal user can also access and configure the scheduler settings by logging on as an administrator. It displays the list of scheduled tasks to be executed at a specific time. Click this module, to schedule the tasks for scanning. You can also edit, delete, or purge the scheduled tasks. With Delete button, you can delete any scheduled task, but Purge button is meant only for outdated schedules, wherein if you click Purge button outdated schedules get automatically deleted.
- Note: The*Schedule(s) outdated displayed at the lower-left corner of the window indicates the outdated schedules. The schedules that were run only once, are called outdated schedules.
- When you click Add task button, the following two tabs appear
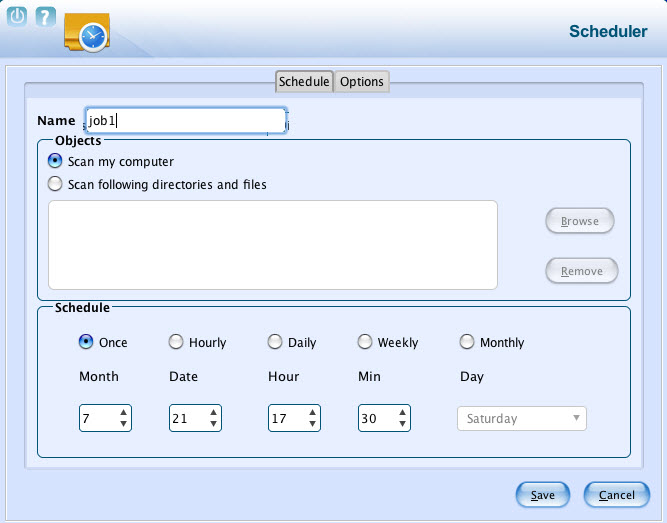
- Schedule:
- It helps you to scan local hard disk/partitions/volumes and selected directories/files. When you select Scan my computer option, eScan scans the entire system. If you want to scan only specific directories and files, click the Scan following directories and files option, and then click the Browse button to select the directories and files of your choice.
- You can schedule the month, date, hour, minute, and day, on which you want to run the task.
- Options:
- It helps you to set an action to be taken by eScan when any virus is detected. Under Settings section, select appropriate check boxes, on which you want to perform scanning.
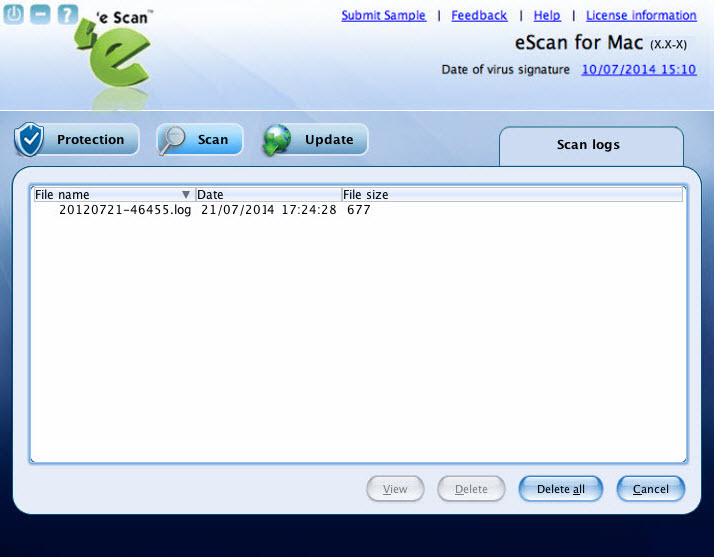
- Logs:
- Click this link, if you want to view and delete the scan log. It displays log list of the scanned files with file name, date, and file size.