From eScan Wiki
| Revision as of 05:33, 13 July 2021 TechContent (Talk | contribs) ← Previous diff |
Revision as of 05:34, 13 July 2021 TechContent (Talk | contribs) Next diff → |
||
| Line 75: | Line 75: | ||
| <p style='font-size:11.0pt;font-family:"Open Sans"'>This section contains a list of Trusted Mac Addresses. A Mac address is a hardware address that uniquely identifies each node of a network.</p> | <p style='font-size:11.0pt;font-family:"Open Sans"'>This section contains a list of Trusted Mac Addresses. A Mac address is a hardware address that uniquely identifies each node of a network.</p> | ||
| - | + | [[Image:Firewall_Settings_Trusted_MAC_Address.JPEG|center]] | |
| <p style='font-size:11.0pt;font-family:"Open Sans"'>This tab has 4 buttons which are as follows:</p> | <p style='font-size:11.0pt;font-family:"Open Sans"'>This tab has 4 buttons which are as follows:</p> | ||
Revision as of 05:34, 13 July 2021
Contents |
Settings
You can configure the firewall setting here. When you click this option, the Firewall Settings (xxx) window appears. The xxx indicates the name of a tab. By default, Zone Rule tab appears. On the Firewall Settings (xxx) window, you have five tabs Zone Rule, Expert Rule, Application Rule, Trusted MAC Address, and Local IP List. Lets discuss them in detail.
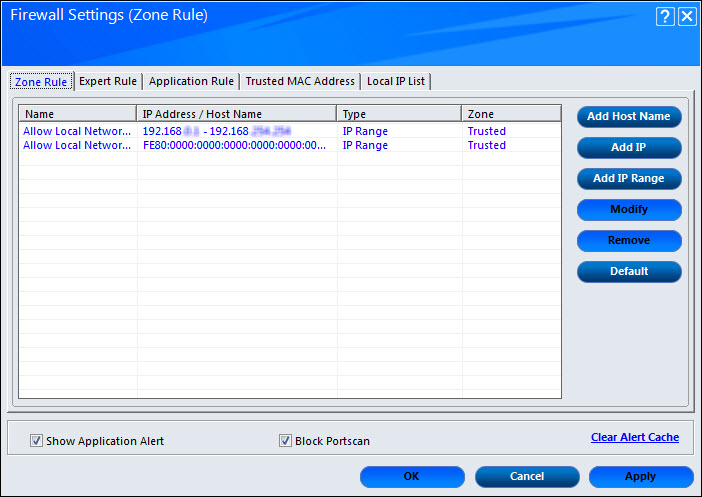
Zone Rule
This tab helps you configure network access rules that specify which IP address, host name, or IP range of computers can access your computer.
This tab includes the following buttons:
- Add Host Name: This button is used to add a zone rule for a given host. To add the zone rule, you must provide name of the host for which you are adding the zone rule; the type of zone, whether it is Trusted or Blocked and specify a name for the zone rule. Clicking OK will add the host in zone rule.
- Add IP: This button is used to add a zone rule for a given IP address. To add the zone rule, you must provide the IP address for which you are adding the zone rule, the type of zone, whether it is Trusted or Blocked and specify a name for the zone rule. By selecting IPv6 Address check box you will enable IPv6 Protocol.
- Add IP Range: This button is used to add a zone rule for a range of IP addresses. To add the zone rule, you must provide the range of IP address for which you are adding the zone rule, start IP address in the range, end IP address in the range; the type of zone, whether it is Trusted or Blocked and specify a name for the zone rule. This has 2 buttons, namely, OK to save changes and Cancel to exit the popup window.
- Modify: This button is used to modify zone rules related to the host name, IP address, or range of IP addresses which is already added in the list. By selecting IPv6 Address check box you will enable Internet Protocol.
- Remove: This button is used to remove the record from list.
- Default: This button is used to load default settings.
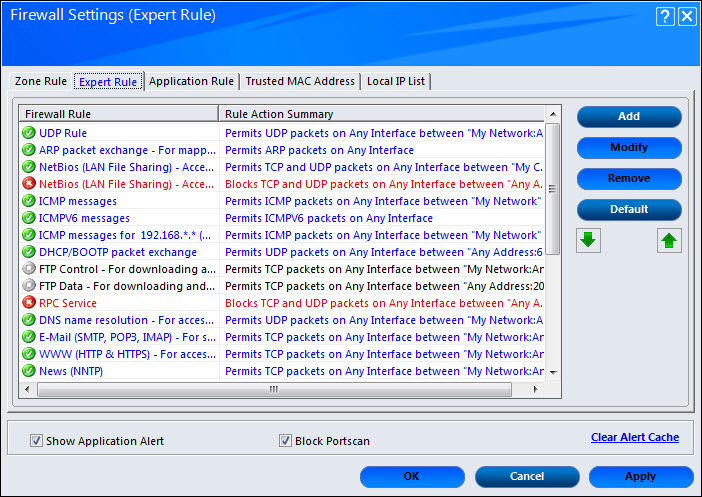
Expert Rule
This tab allows you to specify advanced rules and settings for the firewall. You can configure expert rules on the basis of the various rules, protocols, source IP address and port, destination IP address and port, and ICMP types. You can create new expert rules. However, you should configure these rules only if you have a good understanding of firewalls and networking protocols.
This tab has various button and settings:
- Add: This button adds new rules. We will see how to add new rule in the following Adding New Rule section.
- Modify: This button modifies the already existing rules in the list.
- Remove: This button removes the existing rules from the list.
- Default: This button resets the all the configuration settings.
- Green arrow buttons: This buttons can be used to prioritize the expert rule based on the specific need of the user.
Adding new rule
This section will describe how to add new rule. Click on Add button, Add Firewall Rule window appears.
General
This tab enables you to define rules and its actions. Specify the following field details:
- Rule Name: Type the rule name.
- Rule Action: Click any one of the following types of actions for setting rules.
- Permit Packet: This option is selected by default and it allows you to permit packets.
- Deny Packet: This option allows you to deny packets.
- Protocol: This option lets you to select an appropriate type of protocol from the drop-down list. By default, TCP and UDP is selected.
- Apply Rule On Interface: This option lets you to select Interface to apply the rule. By default, Any Interface is selected.
Source
This tab enables you to type the source IP address and port wherever applicable. You can select the appropriate option. By default, My Network under Source IP Address section and Any under Source Port section are selected.
Destination
This tab enables you to type the destination IP address and port wherever applicable. You can select the appropriate option. By default, My Network under Destination IP Address section and Any under Destination Port section are selected.
Advanced
This tab is specifically meant for ICMP processing, the fields on this tab are available only when you select ICMP from Protocol drop-down list, under General tab.
After configuring all the tab according to your need, click on OK to add the new rule. It will be added in the list.
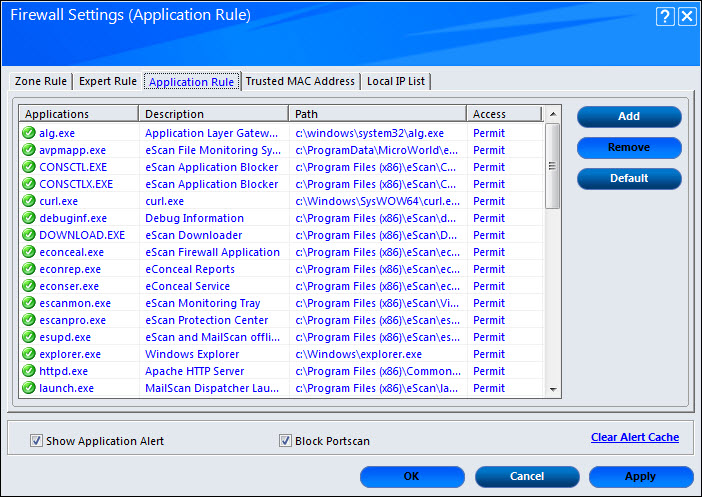
Application Rule
An application rule is based on programs or applications that are allowed to or denied access to the internet or any network‑based service. The Application Rule tab provides you with a default list of rules by eScan and options for configuring application rules.
The context menu shows the following additional options when you right-click any rule in the table:
- Add: Use this option to add new application to the Application Rule list.
- Remove: This option is used to remove any application from the Application Rule list.
- Ask: This option is used to ask for your permission to permit or deny network access.
- Permit: This option is used to permit any added Application for network access.
- Deny: This option is used to deny network access to any application present in the Application Rule list.
- Default: This option is used to reset the configuration to the default.
- Process Properties: This option displays the properties of the selected process or file, which include the name of the file, owner of the file, copyright information, version, and path of the file.
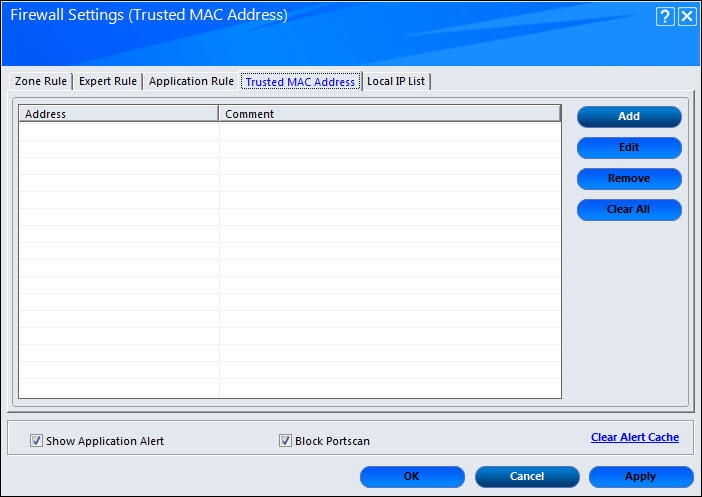
Trusted MAC Address
This section contains a list of Trusted Mac Addresses. A Mac address is a hardware address that uniquely identifies each node of a network.
This tab has 4 buttons which are as follows:
- Add: You can add new Mac address using this button. Once this button is clicked, you will see a New MAC Address dialogue box. Enter the MAC Address and Comment in this dialogue box and click OK.
- Edit: This button edits the existing entries in the list.
- Remove: This button removes the individual existing Mac entries from the list.
- Clear All: This button clears all the Mac addresses in the list.
Local IP List
The local IP address are the devices that are connected to the same network within your organization. This tab displays the list of all local IP addresses.
This tab has 4 buttons which are as follows:
- Add: You can add new IP address using this button. Once this button is clicked, you will see a New IP Address dialogue box. Enter the IP Address in this dialogue box and click OK.</span>
- Edit: This button edits the existing entries in the list.
- Remove: This button removes the existing individual IP entries from the list.
- Clear All: This button clears all the IP addresses in the list.
Show Application Alert
This check box is selected by default and provides you firewall alert when an application is blocked as per an application rule.
Block Portscan
This check box is selected by default and blocks all Portscan attempts made by Hackers.
Clear Alert Cache
You can click this button to clear all the information, such as previous actions taken or blocked programs stored in the firewall's cache.