From eScan Wiki
Revision as of 11:08, 11 October 2010
Index
eScan Features
- What is eScan?
- What is MWL?
- What is eScan Monitor?
- What is Proactive Scanning?
- If I am receiving any infected email, can eScan disinfect that email?
- What is 'Content Security'?
- What is Announcement Server?
- What is a Disclaimer?
- How does Cache Technology work?
- How is eScan different from my current anti-virus product?
- But anti-virus 'X' says that it scans my email messages.How is this different to eScan?
- Is eScan part of MailScan?
- Why is eScan required for MailScan?
- What is the difference between demonstration or evaluation version of eScan software and full license software?
- How do I convert evaluation software to license software?
- Does eScan support database applications like Oracle Database?
- How does eScan scan my emails?
- I see that the antispam automatically creates a Spam folder and e-mail rule in Outlook Express. What e-mail clients get this level of support?
- Can eScan filter other types of accounts like IMAP, Exchange?
- Does eScan scan when I am checking my Hotmail account?
- Does eScan support all email clients?
- What will happen if you have configured eScan to delete an email having restricted content?
- Can I schedule scanning in eScan?
- Will eScan cause instability and performance hit?
- After installing eScan, is there a slowdown in PC performance?
- Does installation of eScan slow down the network?
- Is there a possibility of application timing out when eScan is scanning?
- Does eScan also scan email messages and attachments?
- Does eScan prompts the user if it detects a virus?
- What is Online or Real-Time protection?
- At the time of booting, will eScan scan Memory, Master Boot Record and Partition Table?
- How does Limited Filter Mode Firewall in eScan version 10.0 work?
- How does Interactive Filter Mode Firewall in eScan version 10.0 work?
- When MWAV / Quick Scan is used to scan the system, scanning either gets stuck or takes longer time?
- On Windows 2000 Professional or Server when I click on "Pause Protection" the MWL is not unloaded.
- What is Bkcln.Unknown Virus?
- Is eScan version 10.x Network Access Control (NAC) compliant?
- What is eScan Remote Support (ERS)? How do I login to remote computer. Does it mean that I have to download team viewer to be able to access remote computer?
- Will eScan Anti-Virus Edition (AV) version 10.0 work on Server based Operating System?
- How can I find which product and version of eScan is installed on my computer?
- What are the different type's of Event ID's and their description in eScan client live updater under EMC?
- Does eScan 11 protect users against operating system vulnerabilities?
- What does eScan 11’s “Installation CD with Rescue Disk” mean?
- How do I create the eScan Rescue Disk?
- How does the Whitelisting technology work?
- What is the Laptop Mode feature?
- What is the Gaming Mode feature?
- What is the Virtual Keyboard feature?
- How does the Enhanced Self-Protection feature work?
- What are the advantages of the Folder Protection feature?
- What is the benefit of the Web Phishing feature?
- How will eScan Rescue Disk help me rescue my computer?
- What is eScan??
Answer:
eScan is an advanced, integrated AntiVirus and Content Security product. It will take care of all the dangerous & harmful computer viruses by scanning disks as well as your emails.
Answer:
MWL is the revolutionary "MicroWorld Winsock Layer" developed by MicroWorld. We also refer to this as the MS-MWL or MailScan's MicroWorld Winsock Layer.
Answer:
- eScan Monitor is a true 32-bit device driver that runs in the background, to monitor all the executable files (.exe) operations, whenever they are run or copied on to the system.
- It is loaded automatically when you boot your system.
- If eScan monitor intercepts a virus, it will immediately disinfect the file or otherwise take action as specified by you.
Answer:
Proactive scanning uses intelligent methods to check all executable files, library files and driver files for suspicious programs. For example, a signed file (ie. signed by Verisign) is always whitelisted by the proactive engine. eScan maintains its own whitelisted database (which is regularly auto-updated, along with the anti-virus signatures) in order to keep false positives to a minimum. When a false positive is identified, MicroWorld updates its database as soon as possible, in order to increase the effectiveness and reliability of proactive scanning.
Note: Proactive scanning is not 100% perfect – for this reason, it is always recommended that it be used in conjunction with a malware scanner such as is included in eScan.
Answer:
Yes, eScan resides between your POP3 Server (eg the ISP) and the POP3 client (eg Outlook Express/Netscape on your PC). Hence eScan will scan all your email messages for prohibited Content and Viruses before they reach your InBox.
Answer:
Content Security is a module used by eScan and MailScan to check all your incoming and outgoing traffic for restricted or prohibited content such as abusive words, confidential information, etc.
Answer:
eScan Server (eServ) is termed as Announcement Server. This server is available in
- eScan SMB/SME and Corporate / Enterprise of version 10.x
- eScan Corporate and Enterprise edition of version 9.x
Answer:
A Disclaimer is a customize statement which you can automatically append to all outgoing email messages. All editions of eScan have the facility to insert disclaimers.
Answer:
- Cache Technology is a proprietary technology to ensure that we do not re-scan files which are already scanned.
- This method uses the contents and properties of a file (on both FAT and NTFS) in order to gauge, if a file could possibly be an infected file.
- The cache is independent of both size and attributes & cleared over a period of time.Its also flushed at times a file gets modified.
- Any file that's triggered by our proactive scanner will not be cached - hence the possibility of a malware getting cached is very low.
Answer:
While you can purchase a wide variety of anti-virus products for your Desktop, Notebook and Server platforms, other than a handful of products designed specifically for Mail Servers, none of them contain Content Security capabilities.
Today, this leaves a loop hole in the security of your Desktop and Network that is often exploited by 'hackers'.While other products scan your files, boot sectors, etc. for viruses, eScan also scans all of your email (and attachments) for viruses, worms, trojans, etc. In addition, it does real-time content scanning.
Answer:
More recent versions of some anti-virus products claim to scan your email messages. What all of them do however is scan the emails after they are downloaded into your InBox. This can be way too late, as many viruses now activate as soon as they arrive in the InBox. eScan however scans your email messages before they are downloaded to your Inbox.
Answer:
Yes, each MailScan license is shipped with and installs a single Enterprise edition license of eScan.
Answer:
Many of the features supported by MailScan - such as reporting, Automatic Internet Check and Incremental Updates - either depend upon or are provided by eScan, and thus gives MailScan the ultimate edge over any other anti-virus package available.
Answer:
The software is identical for all versions. However, without a License Key, eScan will expire (stop working) 30-days after installation.
Answer:
Simply purchase and install the Licence Key.
Answer:
Yes, eScan does support all database applications like Oracle and others.
Answer:
eScan includes a component called MailScan-Lite to Scan your emails.
- MailScan-Lite will break the mails into 2 parts i.e the body & the attachment.
- After the disassembly, the body is checked for restricted contents
- Attachments are scanned for viruses.
- After this is done, the email is once again assembled and forwarded to your Inbox.
Answer:
This support is currently available for Outlook Express and Thunderbird client.If you are using some off-brand e-mail client, you can still use eScan's spam filtering, but you will have to create a Spam folder and message rule.
Answer:
eScan filters the incoming POP3 e-mail stream for spam.
- For Exchange, spam and virus scanning filter is possible on the server side using Mailscan for Exchange.
- We cannot filter spam on the client side where emails are downloaded using IMAP. Only virus checking is possible for emails downloaded via IMAP.
- For Exchange, spam and virus scanning filter is possible on the server side using Mailscan for Exchange.
Answer:
but eScan will scan any files you are downloading or saving to the local hard-disk, for viruses, worms, etc.
Answer:
Yes, eScan has been tested with all the commonly used email clients. If you have compatibility issues with a particular email client, please bring it to our attention so that we resolve the issue.
Answer:
eScan will delete the email having restricted content.
Answer:
Yes, you can schedule scanning in eScan.br/>
Answer:
No, since eScan works well above the "raw-packet" layer, MS-MWL - on its own - should not cause any instability and performance hit.Please note that the Anti-Virus & Content-Check components of eScan do use CPU resources and RAM.
Answer:
Generally after any Anti-Virus installation, there will be a minor difference in the systems performance, since the Anti-Virus keeps scanning in the background. But eScan has been designed to take minimum CPU and RAM utilization.
Answer:
Installation of eScan does not slow down the network.
Answer:
We have implemented a variety of methods to ensure that eScan application is "kept alive" when it is receiving and processing emails. This has been extensively tested internally with many different applications. Should a time-out problem occur with a particular application, please contact us immediately so that we may investigate ASAP.
Answer:
Yes, eScan checks email messages and attachments for viruses and spam.
Answer:
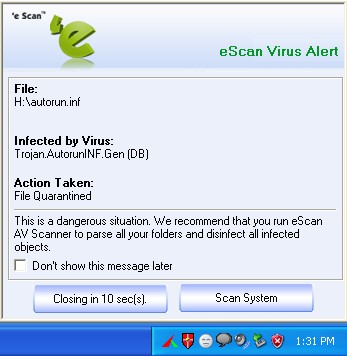
Yes, eScan prompts the user with a virus alert if it detects a virus.
Answer:
eScan monitor is a Real-Time scanner which detects and disinfects viruses online.
Answer:
Yes, eScan scans the local memory while it loads the Monitor after Windows Login. But not the Master Boot Record and Partition Table as Windows does not have access to the same.
Answer:
In the default Limited Filter mode (non-interactive mode), incoming packets from unknown sources (which had no outgoing connection in the first place), are selectively blocked (users are asked for permissions, with default action being blocked). Also, outgoing connections, are allowed (by default) - unless the program happens to be a suspicious program, detected by the proactive scanner.Any programs that connect to the Internet are MD5'ed and in the event that any changes to it's binaries are detected, a question is prompt to the user.However, every connection is logged within eScan databases as well.
This approach has been taken, in view of the fact that most users do not really know whether to click on YES or NO for a question on firewall and want to do away with the queries (like the UAC of Vista).
You can find the ports or the protocols that are whitelisted / blacklisted under the Expert Rule. While you can find the Applications, that are whitelisted / blacklisted under the Application Rule.
To remove the cache, you need to do the following:
- Open the eScan Protection Center
- Click on "Firewall"
- Click on "Settings"
- Click on "Clear Alert Cache"
Note :- When you switch between the "Limited Filter" and "Interactive Mode" the alert cache is cleared automatically.
Answer:
By design, when you select Interactive mode, all outgoing connections will be monitored, unless :
- The program has been white-listed automatically. This means that you have checked the option to create a permanent rule and do not want to be asked again.
- The program has been cache by firewall. This means that it is whitelisted as per the session or you have not checked the option to create a permanent rule and want to be asked again.
- The program has been white-listed automatically. This means that you have checked the option to create a permanent rule and do not want to be asked again.
You can find the ports or the protocols that are whitelisted / blacklisted under the Expert Rule. While you can find the Applications, that are whitelisted / blacklisted under the Application Rule.
To remove the cache, you must do the following:
a. Open the eScan Protection Center
b. Click on "Firewall"
c. Click on "Settings"
d. Click on "Clear Alert Cache"
Note :- When you switch between "Limited Filter" and "Interactive Mode" the alert cache is cleared automatically.
Answer:
This could happen to any Drive or Folder due to lack System rights required by MWAV using the IPC scanning.
Note :- When Quick Scan / MWAV (without any command line parameters) is used to scan the system, it will use the IPC scanning (the title bar or MWAV / Quick Scan will display as "IPC")
To correct this issue, do the following
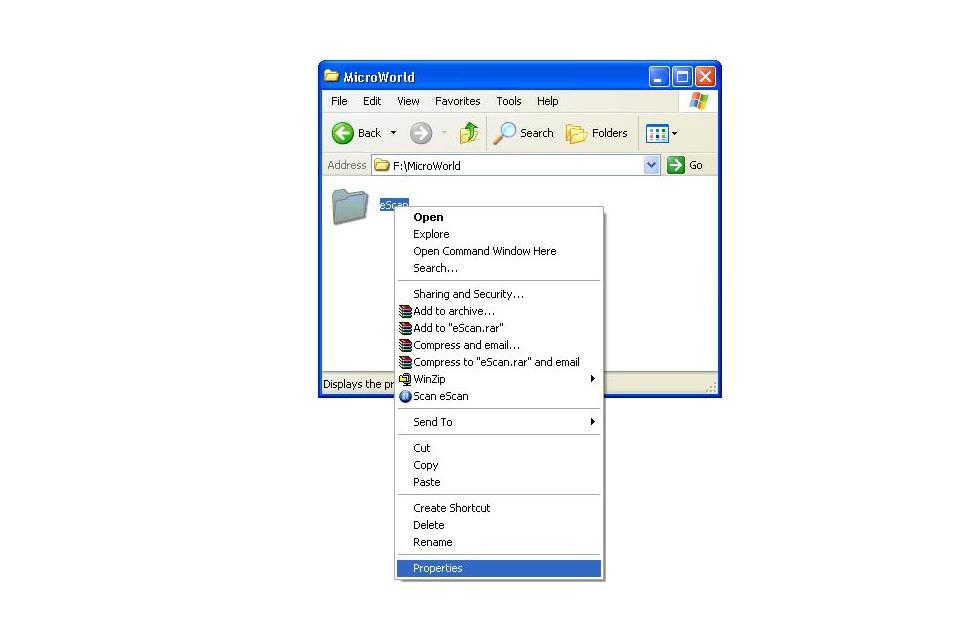
1) Browse to the folder where the Quick scan / MWAV scanning gets stuck or takes longer time to complete. Right click on the folder and click on Properties,
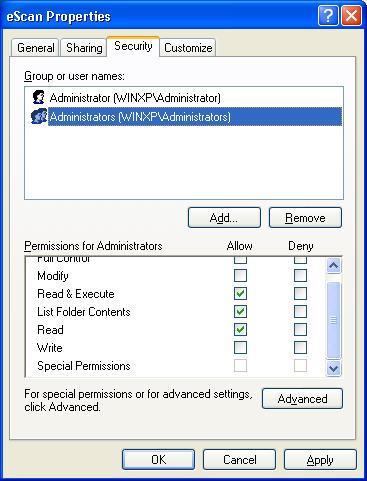
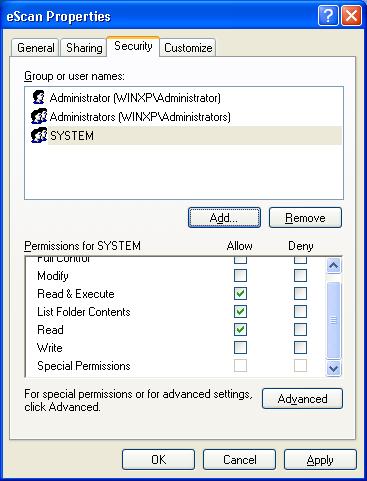
2) In the Properties window, select the Security Tab, System should be present under Groups or user names.
To add System under Groups or user names, click on the Add button,
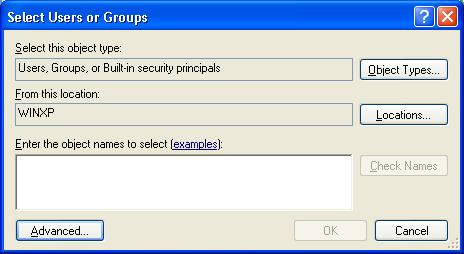
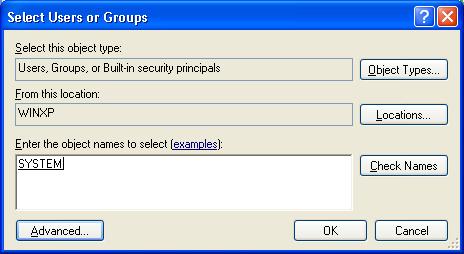
3) In the Select Users and Groups window, click on the Advanced button,
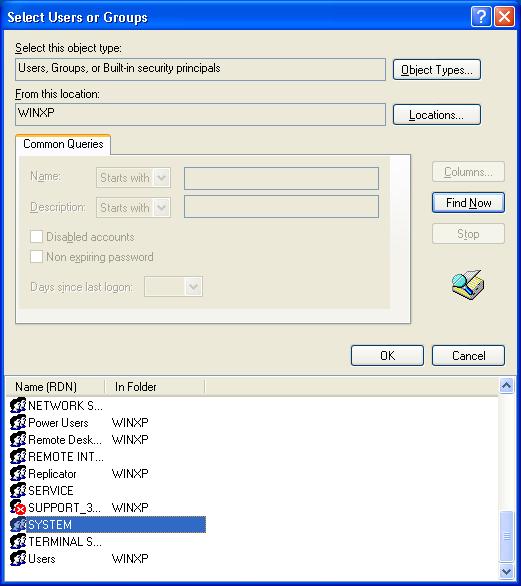
4) and then click on the Find Now button. This will display the list of Users or Groups. Select System from the list and click on the OK button.
5) Click on OK button
6) Then click on the Apply and OK button.
Then restart the scanning using the MWAV or Quick scan.
Answer:
If evaluation or grace period of eScan gets over, then on Windows 2000 Server or Professional it will not stop Web Protection or Mail Anti-Virus. Hence on Windows 2000, layer will remain enabled, even if evaluation or grace period is over. Also it causes problems with few applications of Windows.
On any other operating system, all the features will get disabled.
Answer:
Bkcln.Unknown virus represents a file that was physically present during the scan initialization but the availability of either the file or media was lost while the scan was in progress . This happens normally when a background Anti-Virus deletes the file or a removable drive is unplugged or during the scan the mapping of the drive could have been lost and hence the files are being caught as Bkcln.Unknown which merely indicates the absence of file.
Answer:
The NAC collects all information from the Security Center of Windows Operating System and since we update all the required information like status of Real-Time Monitor if active or not, status of Updates and status of eScan Firewall to the Security Center, we do have Cisco Network Access Control Support.
Answer:
- We have implemented ERS ( eScan Remote support ) feature in eScan itself.
- You just have to right click on "Red shield" icon and click on "eScan Remote support"
- This will be available after applying the latest eScan HOTFIX (Click here for eScan Hotfix Download Link).
- Yes, you have to download Teamviewer to either initiate the connection with client or to Give a remote connection to another person.
Answer:
eScan Anti-Virus Edition (AV) version 10.0 will not work on Server based opetating system.
For Server based operating systems you can choose one of the following product of eScan:
Answer:
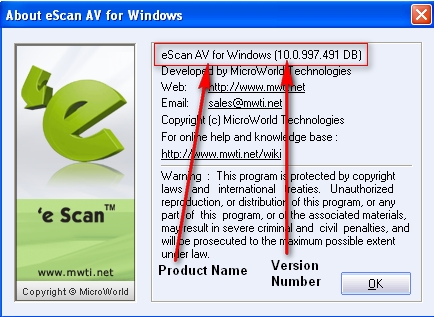
For eScan version 10.x
a. eScan Version 10.x has only one red shield
b. Place the mouse pointer on the red shield ![]() icon, the eScan product name and version number will be displayed.
icon, the eScan product name and version number will be displayed.
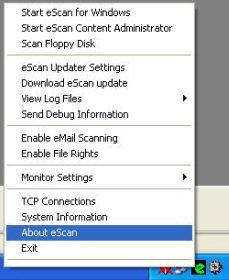
c. Alternately, you can right click on red shield ![]() icon and click “About eScan”
icon and click “About eScan”
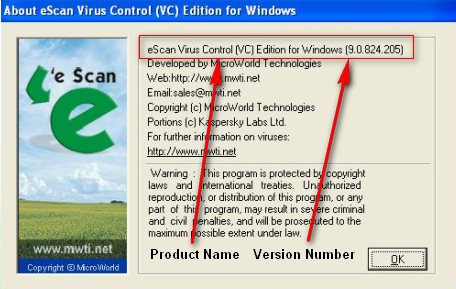
For eScan version 9.x
a. eScan Version 9.x has two icons on the System Tray. A red shield ![]() icon and a green
icon and a green ![]() icon.
icon.
b. Right click on green ![]() icon and click “About eScan”.
icon and click “About eScan”.
c. The eScan Product name and Version number will be displayed on the screen.
Note : If Red icon is not visible in your taskbar. You can find the eScan version from
c:\program files\escan\verinfo.ini
And
c:\windows\win.ini
Answer:
Event ID Description
1 mwav found malware
2 mwav found virus and deleted
3 mwav found virus_and cleaned
4 mwav found adware
5 mwav found error
101 executable blocked.
102 executable allowed.
103 executable from usb blocked.
104 executable already whitelisted and allowed.
105 executable whitelisted by user.
106 application control failed to start.
107 application control error.
108 usb drive blocked.
109 usb drive allowed.
110 usb already whitelisted and allowed.
111 usb drive scan started.
112 usb control failed to start.
113 usb control error.
114 usb device inserted.
115 usb device removed.
116 suspicious application blocked
121 CD/DVD Inserted
122 CD/DVD removed
123 CD/DVD Blocked
124 CD/DVD Allowed
151 eScan Monitor Service Related Errors
152 eScan Monitor Loaded
153 eScan Monitor Unloaded
154 eScan Updates are done
155 eScan Updates are failed
156 eScan Monitor Settings are modified
157 eScan Monitor backup taken
158 eScan Monitor backup restored
159 eScan Monitor file restored
160 eScan Monitor error
181 eScan Monitor file infected
182 eScan Monitor file renamed
183 eScan Monitor file deleted
184 eScan Monitor file disinfected
185 eScan Monitor file suspected
186 eScan Monitor file corrupted
187 eScan Monitor file scan cancelled
188 eScan Monitor file access denied
189 eScan Monitor file print copy failed
190 eScan Monitor file clean
191 eScan Monitor file not scanned
192 eScan Monitor file scan timed out
193 eScan Monitor file scan failure
250 Website visited
251 Website Blocked
300 Mail Virus Quarantined
301 Mail Spam Quarantined
302 Mail Reserved Attachment quarantined
303 Mail partial message quarantined
304 Mail corrupted message quarantined
305 Mail HOP Count message quarantined
306 Mail unscanned message quarantined
307 Mail dangerous attachment quarantined
308 Mail blank attachment quarantined
309 Mail TNFF attachment quarantined
331 Mail Virus deleted
332 Mail Spam deleted
333 Mail Reserved attachment deleted
334 Mail Partial message deleted
335 Mail Unscanned message deleted
336 Mail dangerous attachment deleted
361 Mail clean
362 Mail Virus detected and cleaned
363 Mail still infected
364 Mail attachment replaced
501 Scheduled mwav found malware
502 Scheduled mwav found virus and deleted
503 Scheduled mwav found virus_and cleaned
504 Scheduled mwav found adware
505 Scheduled mwav found error
506 Scheduled mwav started
507 Scheduled mwav summary
Answer:
eScan 11 automatically checks the Microsoft® Web site and downloads critical hotfixes and updates for the Windows® operating systems as and when they become available. Most new strains of malicious software, such as Rootkit.Stuxnet.A and Rootkit.TmpHider exploit the vulnerabilities in operating systems. eScan 11 ensures that the computer on which it is installed has the latest hotfixes and updates installed on it. Thus, eScan prevents malicious software that exploit vulnerabilities in the operating system from infecting the computer and helps users protect their data from hackers and other security threats.
Answer:
eScan 11's product installation CD comes with a set of installation setup files and a bootable Rescue Disk. The bootable Rescue Disk enables the user to clean-boot the computer if the operating system fails to load on it.
Answer:
The eScan Rescue Disk enables the user to clean boot the computer if the operating system fails to load on it. You can create the eScan Rescue Disk CD, if required.
To create the eScan Rescue Disk CD, perform the following steps.
Method 1
- Download the eScan Rescue Disk ISO Image file from the eScan Web site. To download the image file, visit the download Web page.
- Burn the ISO image on a CD by using a CD burning software.
You can also create the eScan Rescue Disk ISO file by following the steps given on the eScan Rescue Disk Web page.
Answer:
Anti-Spam maintains a list of allowed domain names or e-mail addresses that can bypass the spam filtering options. The Whitelisting technology allows e-mails from senders, whose e-mail address or domain name is in the whitelist, to be downloaded to the recipient’s inbox and prevents them from being blocked.
Answer:
eScan 11 includes the automatic detection of Laptop Mode feature, which is a power-saving feature that provides unmitigated battery time for laptops. Whenever a user switches to the Laptop Mode, eScan 11 automatically detects this change and prevents memory intensive processes like scheduled scans from running. Note that eScan's real-time protection remains active while the laptop is in the Laptop Mode.
Answer:
eScan 11 includes a Gaming Mode, which provides an uninterrupted gaming experience to users while they are running gaming applications in the full screen mode. The benefit of the Gaming Mode lies in how eScan handles alerts while a user is playing a game. Normally, when a user switches on a computer running eScan, the real-time protection module starts running in the background. Now, when a user starts a game, eScan may display alerts and notifications, which may affect the user's game. The Gaming Mode in eScan 11 has been designed to overcome this problem. Whenever a user runs a game on a computer, eScan 11 automatically enables the Gaming Mode, which prevents alerts and notifications from being displayed. eScan automatically disables this mode when the user exits the gaming application. Thus, the Gaming Mode provides the user with an uninterrupted and seamless gaming experience.
Answer:
eScan 11 provides users with a Virtual Keyboard that helps them avoid using their keyboard to enter confidential information. This is highly useful because it has several security benefits. Malware writers create malware because of their need to obtain a payload. The payload for a password-stealing Trojan may be the authentication information of a user's online banking account. Malware often include keyloggers, which are programs designed to capture the keystrokes on the computer on which they are installed. Whenever a user fills in details such as user name or password on an online form, the keylogger obtains this information and then sends it to the hacker. The user interface of eScan's Virtual Keyboard simulates the user's keyboard and acts as a secure mechanism for the user to enter sensitive information, such as credit card details and banking passwords, without any fear of data theft due to keyloggers.
Answer:
eScan 11 comes with the enhanced Self Protection feature that protects critical eScan files and folders from being deleted or modified. Some new generation malware try to infect computers by deactivating the Anti-Virus software running on them. They try to achieve this by either disabling the Anti-Virus software or by deleting critical files that are necessary for running the Anti-Virus software. The enhanced Self Protection feature of eScan 11 prevents malware from either disabling eScan or deleting its critical files thus keeps computers safe from infections.
Answer:
eScan 11 includes the new Folder Protection feature. This feature helps users protect specific files and folders from being modified or deleted. The main advantage of this feature is that it prevents the specified files from being infected by malicious software. Another advantage of this feature is that files and folders that are protected cannot be deleted unless the folder protection is turned off. This helps users safeguard their confidential data from infections by malware and accidental deletions.
Answer:
eScan 11 includes a Web Phishing Filter that protects the user from phishing Web sites. When it is enabled, the Web Phishing Filter checks and informs the user whether the Web site that the user is currently visiting is genuine or not. This safeguards the user from inadvertently disclosing any digital identity details or financial information on fraudulent Web sites.
Answer:
You can use the bootable Rescue Disk to boot your computer if the operating system cannot be loaded on it. The Rescue Disk also includes the eScan Anti-Virus Toolkit (formerly MWAV), which runs automatically when you boot the computer using the disk. It helps you scan the computer's memory, registry, startup folders, system folders, and drives for viruses and spyware. In addition, it helps you run the Command.exe file and execute commands for formatting the hard disk, partitioning any drive, or checking the hard disk for errors.